
Imagine the chaos that would ensue if the keys to your company’s facilities were misplaced, duplicated without authorization, or fell into the wrong hands. The security of your organization’s assets, sensitive information, and even the safety of your employees could be compromised. That’s where a solid employee key policy comes into play. In this blog post, you’ll discover how to create and implement a comprehensive employee key policy that keeps your organization secure and prevents unauthorized access.
We’ll guide you through the process of developing a robust employee key policy, designing a master key structure, enforcing key holder responsibilities, and training and educating employees about key control policies. By the end of this blog post, you’ll have the knowledge and tools to effectively manage your company’s keys, ensuring the security and integrity of your organization’s assets and information.
Key Takeaways
- Develop a robust key control policy by assessing access requirements, establishing authorization protocols and implementing a patented key control system.
- Monitor key distribution and usage through tracking, security measures and management systems.
- Train employees on policies to promote security awareness & streamline processes with online forms for timely returns of keys.
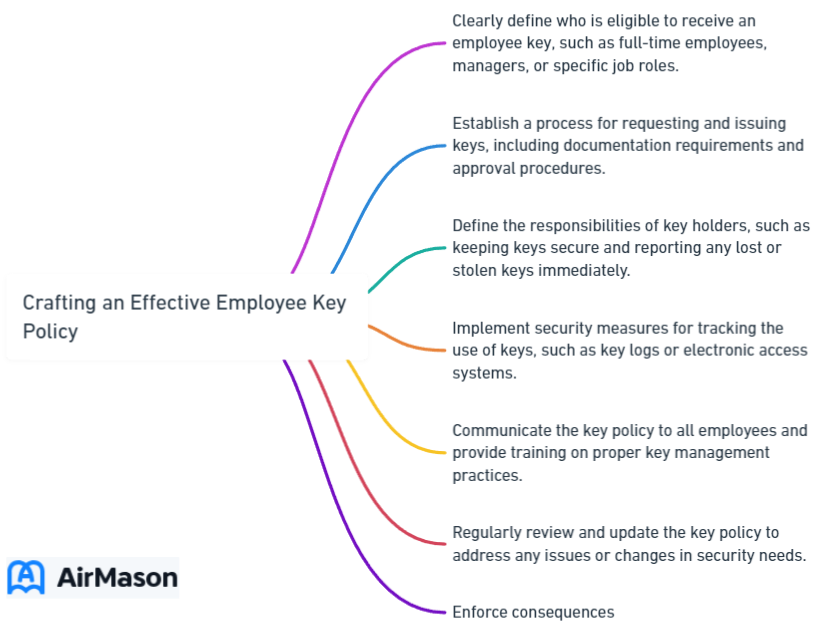
Developing a Robust Key Control Policy for Employees
A well-defined key control policy is a vital element in maintaining the security of your organization’s facilities and preventing unauthorized access. A comprehensive key control policy can help you effectively manage issued keys, track key distribution and usage, and establish clear authorization protocols for key issuance.
In order to create a comprehensive key control policy, there are nine essential steps to consider:
- Assess employee access requirements
- Establish clear authorization protocols
- Implement a patented key control system
- Design a master key structure
- Enforce key holder responsibilities
- Train and educate employees on key control policies
- Manage key requests and returns
Adhering to these steps will bolster the security and effectiveness of your key control program.
Assessing Employee Access Requirements
Constructing a functional key control system involves the following steps:
- Identify and document the roles and responsibilities of each employee to ensure they are provided with the required access to fulfill their job duties, including access to master key systems.
- Implement a key control system that meets your organization’s specific needs by managing employee access using key tracking software.
- Perform regular audits to ensure the accuracy and security of your key control system.
- Institute online forms and procedures to streamline the process of requesting and issuing keys.
- Ensure the timely return of keys to maintain the integrity of your key control system.
By following these steps, you can establish an effective key control system for your organization.
Working with a locksmith who has a list of approved persons is of utmost importance in preventing unauthorized duplication of keys and ensuring that the key control office is aware of all key distributions. Such a partnership with a certified locksmith provides the assurance that keys are obtained only through reliable sources and the distribution process is carefully monitored.
Establishing Clear Authorization Protocols
An effective key control policy fundamentally hinges on clear authorization protocols. Key requests must strictly adhere to the policy’s procedures and should be formally made using the dedicated key request form. Only those who are authorized to do so within their respective departments should request for keys or lock changes. Unauthorized individuals should not make such requests..
Delegation of authority for the prevention of unauthorized access and duplication of keys should be done in writing. This should be done on official stationary and have the department head’s original signature. Under no circumstances should keys be issued to students.
When assuming custody of a master key, individuals must sign a statement confirming their responsibility for the proper use, storage, and return of the key, as well as obtaining a replacement key if needed, upon leaving the organization or changing their position.
Implementing a Patented Key Control System
![]()
A patented key control system is a powerful tool to ensure the security and control over key distribution, preventing unauthorized duplication and access. The use of patented key control products can significantly enhance your organization’s security. These products deter key holders from replicating the key and provide the authority to legally prosecute any patent infringers.
Williams College, for example, maintains a patented keyway to provide safety and security for its campus facilities. Such patented key systems are protected by patents, prohibiting the production of unauthorized physical copies of the keys and ensuring the security of the premises.
Partnering with Authorized Locksmiths
Collaborating with certified locksmiths ensures that keys can be acquired only through reliable sources and that the distribution of keys is carefully monitored. The locksmith should have a system in place for verifying identification. All information relevant to the keys being cut should be accurately recorded. They can audit the keys that contracted locksmiths cut to ensure adherence to all control policies.
By working closely with a reliable locksmith, your organization can:
- Develop a key control plan in unison
- Formulate a master key system that meets its unique security needs
- Verify identification during the key cutting process to guarantee that only those who are authorized are given keys, ensuring the security of your organization’s assets and information.
Monitoring Key Distribution and Usage
Monitoring key distribution and usage is a crucial step in maintaining the security of your organization’s facilities and assets. This involves tracking who has access to keys, ascertaining the number of copies in existence, and instituting measures to prevent unauthorized access. Recommended practices for overseeing key distribution in businesses include recording all key issuances and associated serial numbers, implementing a key management system, integrating key management with existing infrastructure, documenting key life cycle management, and establishing a vendor compliance program.
Utilizing key control systems, monitoring software, usage tracking, and regular key rotation can effectively monitor key usage in a large company and prevent issues related to lost keys.
Designing a Master Key Structure

A master key system is an effective way of controlling access to different areas of a building. It involves the use of special keys that grant varying levels of authority. Designing a master key structure involves creating a tiered access system that defines different levels of access for employees and integrates electronic access controls for increased security. This ensures that employees have the appropriate level of access to company facilities, preventing unauthorized access and maintaining security.
A tiered access structure allows your organization to effectively manage employee access according to their job responsibilities and requirements. This structure offers several benefits:
- Enhances overall security
- Provides control over access
- Enables the designation and restriction of access to specified areas or assets
- Facilitates a tiered access system
Defining Access Levels
Establishing access levels guarantees that personnel are provided with the suitable level of access to corporate facilities, thwarting any unauthorized access and sustaining security. The typical types of access levels in a company facility comprise:
- Discretionary Access Control (DAC)
- Role-Based Access Control (RBAC)
- Attribute-Based Access Control (ABAC)
- Mandatory Access Control (MAC)
- Rule-Based Access Control (RuBAC)
These access levels assist organizations in regulating who has access to data or resources within their facility.
Access levels can be assigned to different employee roles by following these steps:
- Inventorize your systems
- Analyze your workforce and create roles
- Assign people to roles
- Define access levels
- Assign access levels to roles
Implementing role-based access control (RBAC) enables organizations to effectively assign access levels to different employee roles, ensuring that employees have access level appropriate to their job responsibilities.
Integrating Electronic Access Controls
An electronic access control (EAC) system, also known as an access control system, is an essential component of an organization’s security program. It requires a card, fob, fingerprint, or other credentials to unlock a door and restrict access based on time, date, and credentials. Integrating electronic access controls into your master key structure provides time-based access and a record of activity for enhanced security.
The audit trail in an EAC system serves as a powerful instrument to investigate crime and loss, as it maintains a record of when and by whom access was gained to specific areas. Incorporating electronic access controls into your organization’s key control policy can strengthen security further and maintain a comprehensive overview of access events.
Enforcing Key Holder Responsibilities

Key holder responsibilities are of utmost importance in preserving the safety of your organization’s premises. A comprehensive key control policy should be implemented to ensure that key recipients take proper care of them and do not leave them unsupervised. Enforcing key holder responsibilities involves having employees sign a key holder agreement outlining their obligations and ensuring compliance with the requirement to promptly report any lost or stolen keys.
Holding key holders accountable for their actions helps your organization to prevent unauthorized access and maintain the security of its facilities and assets. This not only protects your organization but also establishes a culture of responsibility and security awareness among employees.
Signing the Key Holder Agreement
A key holder agreement is of paramount importance in order to safeguard the organization’s assets and ensure the security of the premises. It clearly delineates the responsibilities of the key holder and any potential consequences in the event of misuse or loss of the keys. Employees, upon signing the agreement, confirm their understanding of the key control policy and their commitment to comply with it.
The key holder agreement not only establishes usage expectations for company keys but also holds employees accountable for the proper handling and care of these keys. By outlining the responsibilities and consequences associated with key usage, organizations can better maintain control over key distribution and ensure the security of their facilities.
Reporting Lost or Stolen Keys
It is imperative to report lost or stolen keys without delay in order to ensure security and preclude unauthorized access to company premises. The relevant department or authority, such as the Campus Police Department or the Lock Shop, should be notified based on the company’s policy, and the report should be made within 24 hours of discovering the incident.
Prompt reporting of lost or stolen keys allows your organization to take immediate action to mitigate potential security risks and prevent unauthorized access to sensitive areas. Implementing a key control policy that emphasizes the importance of reporting lost or stolen keys helps your organization maintain a secure environment and protect its assets and information.
Training and Educating Employees on Key Control Policies

In order to ensure that regular training sessions are conducted and a security-conscious culture is fostered within the organization, it’s essential to provide employees with education and training on key control policies. This not only equips employees with the necessary knowledge and skills to properly handle and care for company keys but also instills a sense of responsibility and awareness regarding the importance of security.
Conducting regular training sessions and promoting a security-conscious culture ensures that employees are well-informed about significant control policies, protocols, and beneficial practices for key utilization. This, in turn, strengthens the security of your organization and minimizes the risk of unauthorized access or key misuse.
Store Policy for Employees
Our store prides itself on fostering a positive and inclusive work environment through our comprehensive “Store Policy for Employees.” This policy is designed to ensure that all team members are aware of their rights, responsibilities, and the expectations we have for maintaining a productive and harmonious workplace. From guidelines on work schedules to performance expectations and employee benefits, the “Store Policy for Employees” serves as a crucial resource for everyone in our organization. By adhering to this policy, we aim to create a workplace where every employee feels supported and valued, contributing to the overall success of our team and the satisfaction of our customers
Conducting Regular Training Sessions
Holding regular training sessions ensures that personnel are cognizant of essential control policies, processes, and optimal practices, including the utilization of keying charts and proper key utilization. Effective key control training sessions should cover various topics, such as:
- The use of restricted, uniquely marked keys
- Investing in a patented key system
- Developing a master key system
- Rekeying your facility occasionally
- Providing training sessions for newly onboarded staff
Assessing the efficacy of key control training sessions can be done using a combination of quantitative and qualitative metrics, such as:
- Test scores
- Course completion rates
- Job performance
- Surveys
This ensures that employees are well-equipped to handle and maintain the security of company keys.
Promoting a Security-Conscious Culture
Fostering a security-conscious culture within your organization involves continuous dialogue and reinforcement of the importance of security measures. Encouraging employees to take necessary precautions to protect company assets and information helps to create an environment where security is a top priority.
Several organizations, such as MongoDB and AlertMedia, have established successful cybersecurity cultures by developing comprehensive cyber-awareness programs, establishing robust safety cultures, and focusing on awareness and accountability. Promoting a security-conscious culture within your organization ensures that employees take their key control responsibilities seriously and contribute to the overall security and integrity of your facilities.
Managing Key Requests and Returns
Managing key requests and returns is an important aspect of maintaining an effective key control policy. Here are some strategies to help your organization effectively manage its key control system:
- Streamline key requests and returns with online forms.
- Implement key control systems for timely returns.
- Ensure proper documentation and tracking of key issuance and retrieval.
By following these strategies, you can streamline your key control process and ensure the security of your organization’s keys.
Ensuring that all keys issued to employees are returned before their employment ends helps your organization maintain control over key distribution and prevent unauthorized access to its facilities and assets. This not only helps to maintain the security of your organization but also ensures that employees are held accountable for their actions and the proper handling of company keys.
Streamlining Processes with Online Forms

Utilizing online forms to streamline the key request and return process offers several advantages, such as:
- Simplifying the submission and processing of requests
- Reducing errors and ensuring accurate data
- Enabling automated workflows to eliminate manual handling
- Reducing processing time
- Making the processes more convenient and accessible for both employees and administrators.
Online platforms such as Google Forms, Microsoft Forms, and Jotform can be used to create key request and return forms that are tailored to your organization’s specific needs. Online forms that incorporate essential elements like building and room information, key numbers, quantity of keys requested, and contact information facilitate efficient management of key requests and returns, contributing to a secure and efficient system.
Implementing Key Control Systems for Timely Returns
Implementing key control systems for timely returns is crucial to maintain security and prevent unauthorized access to company facilities. Utilizing key control systems like key management systems and logical hardware keying design ensures that keys are promptly returned upon termination or change in access requirements.
In addition to streamlining the key request and return process, implementing key control systems can help your organization maintain a secure environment, protect its assets and information, and hold employees accountable for their actions and the proper handling of company keys.
Summary
In conclusion, implementing a comprehensive key control policy is essential to maintaining the security of your organization’s facilities and preventing unauthorized access. By following the steps outlined in this blog post, such as developing a robust key control policy, designing a master key structure, enforcing key holder responsibilities, and providing training and education on key control policies, you can effectively manage your company’s keys and ensure the safety and integrity of your organization’s assets and information.
Take action today to strengthen your key control policy and promote a security-conscious culture within your organization. The success of your company’s security program depends on the diligence and commitment of your employees in upholding key control policies and procedures. Embrace the importance of key control and empower your employees to take responsibility for the security of your facilities and assets.
Policy for Working Remotely
Our “Policy for Working Remotely” is designed to provide clear guidelines and expectations for employees engaging in remote work. This policy outlines the parameters and responsibilities associated with working outside the traditional office environment. It addresses key considerations such as communication protocols, performance expectations, and the use of company resources. Adherence to the “Policy for Working Remotely” ensures a seamless integration of remote work into our operational framework, promoting productivity and maintaining a cohesive work culture. Employees are encouraged to familiarize themselves with this policy to foster a successful and efficient remote work experience.
Frequently Asked Questions
What is the key control policy?
A key control policy ensures the safety, security and privacy of property and people by giving your organization control over access to spaces and assets.
What are the responsibilities of key control?
Key control is a system used to monitor the use of keys, ensuring only authorized people have access to company property and secure areas. It provides an extra layer of security to help protect private spaces and assets from potential cybercrime threats.
What are the key control methods?
The key control methods typically involve locks on the doors, connected to a computer that logs entries and exits. This allows hotels to track occupancy and ensure no one is staying beyond their reservation.
What is the physical key management process?
Physical key management is the collective process of securing, tracking, and distributing physical keys in order to reduce overhead and control access control costs.
What are the key components of a comprehensive key control policy?
A comprehensive key control policy should include assessing employee access requirements, establishing authorization protocols, implementing a key control system, designing a master key structure, enforcing key holder responsibilities, training employees on policies, and managing key requests and returns.